

SSP Consulting
Structured Systems Planning| Insightful & Holistc IT Services
SSP: A modern approach to IT strategy
SSP adopts a holistic approach, viewing business and IT systems as a unified ecosystem. With an insightful understanding of end-users, IT systems, and controls, SSP crafts a comprehensive strategy that synchronizes technology with business goals.
This all-encompassing methodology enables thorough analysis across all system components, uncovering hidden inefficiencies and opportunities for enhancement. SSP ensures optimal synergy by examining the interplay between various elements, driving overall system effectiveness and business performance.

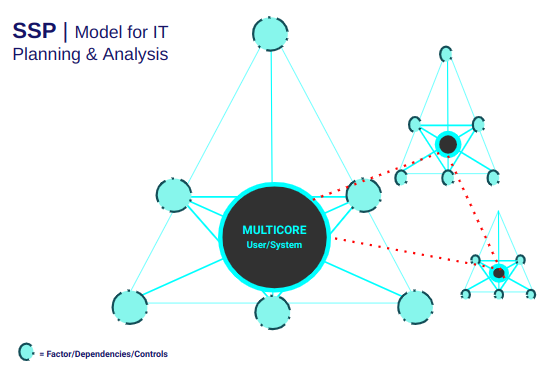
SSP: Mulitple Mission-Critical Cores in Focus
Core components of a business system:
- People (End-users)
- Systems
- Controls
These components are interconnected through:
- Technology Resources
- Workflows
- Decision-making processes
Goals of SSP:
- Ensure stable IT-Business alignment
- Facilitate seamless IT-Business alignment
- Optimize IT Systems to support business needs
IT Solutions



- Systems Engineering and Administration
- Helpdesk Analysis and Support
- User training and documentation
- IMAC-D
- Lifecycle Management
- Software license compliance and optimization
- Security Compliance
- Monitoring and management infrastructure
- Security audits and implementation of cybersecurity measures
- Cloud integration and optimization
IT Engineering: People and Business First

Comprehensive IT Solutions for Modern Businesses: Enhancing Security and Streamlining Workflows
In today's digital landscape, businesses rely heavily on robust IT infrastructure to maintain productivity, protect sensitive data, and stay competitive. Our comprehensive suite of IT Engineering and systems administration services is designed to address these critical needs, with a focus on safeguarding company information and optimizing workflow efficiency for end-users and staff members.
Systems Engineering and Administration
Our expert team provides top-tier systems engineering and administration services, ensuring that your IT infrastructure operates seamlessly. We design, implement, and maintain scalable solutions tailored to your business needs, constantly monitoring and optimizing performance to prevent downtime and enhance productivity.
Helpdesk Analysis and Support
Our dedicated helpdesk team offers rapid, efficient support to resolve technical issues promptly. By leveraging advanced analysis tools and methodologies, we identify and address potential problems before they impact your operations, minimizing disruptions and maintaining a smooth workflow for your staff.
User Training and Documentation
We believe that empowered users are more productive and less prone to security risks. Our comprehensive training programs and clear, accessible documentation enable your staff to make the most of your IT resources while adhering to best practices in data protection and efficient workflow management.
Software and Business Applications
We provide expert support for a wide range of software and business applications, ensuring that your team has access to the tools they need to excel. Our services include:
Installation and configuration of essential productivity suites like Microsoft Office (Word, Excel, PowerPoint, Outlook)
Implementation and support for enterprise resource planning (ERP) software such as SAP and Oracle
Software license compliance management and optimization to ensure legal use and cost-effectiveness
Device Support
Our device support services cover a broad spectrum of hardware and operating systems, including:
Hardware troubleshooting and repair for PCs, laptops, tablets, and smartphones
Operating system updates and maintenance for Windows, macOS, various Linux distributions, and network equipment
Proactive maintenance to extend device lifespan and optimize performance
User Account Management
We implement robust user account management solutions, utilizing industry-standard technologies such as Active Directory, Azure AD, and LDAP. This ensures secure access to resources while maintaining ease of use for your staff.
VPN and Remote Access Setup
In an era of increased remote work, we provide secure and reliable VPN and remote access solutions. Our expertise covers popular platforms like Cisco AnyConnect, OpenVPN, and FortiClient, enabling your team to work efficiently and securely from any location.
By leveraging our comprehensive IT services, your business can enjoy:
- Enhanced data protection through the implementation of best practices and cutting-edge security measures
- Improved workflow efficiency, allowing your staff to focus on core business activities
- Reduced downtime and technical issues, leading to increased productivity
- Cost optimization through efficient resource allocation and license management
- Scalable solutions that grow with your business needs
IT Asset Management (ITAM): Protecting Systems and Data, Increasing Vaule

Technology Asset Management: Maximizing Efficiency and Security.
In today's technology-driven business landscape, effective IT Asset Management (ITAM) is crucial for organizations to maintain operational efficiency, ensure security compliance, and optimize costs. This comprehensive approach encompasses several key areas that work together to create a robust ITAM strategy.
IMAC-D: The Backbone of Asset Management
IMAC-D, which stands for Install, Move, Add, Change, and Dispose, forms the foundation of IT asset management. This systematic approach ensures that all IT assets are tracked and managed throughout their entire lifecycle:
- Install: Properly deploying new assets and integrating them into the existing infrastructure.
- Move: Efficiently relocating assets while maintaining accurate inventory records.
- Add: Incorporating new components or expanding existing systems seamlessly.
- ange: Updating or modifying assets to meet evolving business needs.
- Dispose: Securely and responsibly retiring outdated or unnecessary assets.
By implementing a strong IMAC-D process, organizations can maintain an accurate inventory, reduce downtime, and ensure that all assets are accounted for and utilized effectively.
Lifecycle Management: Maximizing Asset Value
Effective lifecycle management is essential for extracting maximum value from IT assets while minimizing risks and costs. This process involves:
- Planning: Identifying business needs and selecting appropriate assets.
- Procurement: Acquiring assets through cost-effective and compliant methods.
- Deployment: Efficiently integrating new assets into the existing infrastructure.
- Maintenance: Regular upkeep to ensure optimal performance and longevity.
- Optimization: Continuously assessing and improving asset utilization.
- Retirement: Securely decommissioning and disposing of obsolete assets.
By carefully managing each stage of an asset's lifecycle, organizations can reduce total cost of ownership, improve return on investment, and ensure that their IT infrastructure remains aligned with business objectives.
Software License Compliance and Optimization
Managing software licenses is a critical component of ITAM, with significant financial and legal implications. Effective software license management involves:
- Inventory: Maintaining an accurate count of all software installations and licenses.
- Compliance: Ensuring that all software usage adheres to licensing agreements.
- Optimization: Identifying underutilized licenses and reallocating them to maximize value.
- Cost management: Negotiating favorable terms and avoiding unnecessary purchases.
- Audit readiness: Maintaining documentation to easily demonstrate compliance during audits.
By optimizing software license management, organizations can avoid costly penalties, reduce unnecessary expenditure, and ensure that software resources are used efficiently across the enterprise.
Security Compliance: Safeguarding Assets and Data
In an era of increasing cyber threats, security compliance is a crucial aspect of IT asset management. This involves:
- Asset visibility: Maintaining a comprehensive inventory of all hardware and software assets.
- Vulnerability management: Regularly assessing assets for security weaknesses and applying necessary patches.
- Access control: Implementing and managing user permissions to prevent unauthorized access.
- Data protection: Ensuring that sensitive information is properly secured throughout an asset's lifecycle.
- Compliance monitoring: Continuously tracking adherence to relevant security standards and regulations.
- Incident response: Developing and maintaining plans to address security breaches quickly and effectively.
By integrating security compliance into ITAM practices, organizations can significantly reduce their risk of data breaches, protect sensitive information, and maintain trust with customers and stakeholders.
Conclusion
Effective IT Asset Management is essential for modern businesses to thrive in a digital environment. By implementing robust IMAC-D processes, managing asset lifecycles, optimizing software licenses, and ensuring security compliance, organizations can maximize the value of their IT investments while minimizing risks and costs. As technology continues to evolve, a comprehensive ITAM strategy will remain crucial for maintaining a competitive edge and ensuring long-term success.
Network Planning & Maintenance: Moving data and empowering your business cores

Network Planning and Maintenance: Building Robust and Secure IT Infrastructure
In today's interconnected business world, a well-planned and maintained network is crucial for organizational success. This article explores key aspects of network planning and maintenance, including physical infrastructure, cloud integration, and security measures.
Physical LAN Connections: The Foundation of Network Infrastructure
Building a reliable physical Local Area Network (LAN) is the cornerstone of any robust IT infrastructure. This involves:
- Structured cabling: Implementing high-quality Ethernet cabling (e.g., Cat6a or fiber optic) for fast, reliable connections.
- Network switches: Deploying enterprise-grade switches from vendors like Cisco, Juniper, or HP for efficient data routing.
- Patch panels and racks: Organizing network equipment for easy management and scalability.
- Wireless access points: Strategically placing Wi-Fi access points for comprehensive coverage.
By carefully designing and implementing physical LAN connections, organizations can ensure a solid foundation for their network infrastructure.
Microsoft Azure Cloud Support and Hybrid Solutions
As businesses increasingly adopt cloud technologies, Microsoft Azure has become a popular choice for cloud computing. Azure offers:
- Scalable infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) solutions.
- Integration with on-premises systems for hybrid cloud setups.
- Advanced security features and compliance certifications.
- Global network of data centers for improved performance and redundancy.
Implementing Azure alongside on-premises infrastructure creates a powerful hybrid environment, allowing organizations to leverage the benefits of both cloud and traditional IT setups.
Hybrid and Collocated Data Center Setup
Many organizations opt for a hybrid approach, combining on-premises infrastructure with cloud services and collocated data centers. This setup offers:
- Increased flexibility and scalability.
- Improved disaster recovery and business continuity.
- Optimized performance through strategic data and application placement.
- Cost savings by leveraging cloud resources for variable workloads.
When setting up collocated data centers, considerations include power requirements, cooling systems, physical security, and connectivity options.
Network Equipment: Fortinet, Cisco, and Juniper
Leading network equipment providers offer a range of solutions for building robust networks:
- Fortinet: Known for its next-generation firewalls and unified threat management systems.
- Cisco: Offers a comprehensive range of networking equipment, including routers, switches, and security appliances.
- Juniper: Provides high-performance networking solutions, particularly suited for service providers and large enterprises.
Choosing the right mix of equipment from these vendors ensures a powerful, secure, and scalable network infrastructure.
Server Storage and Servers: Dell EMC and HP
Enterprise-grade servers and storage solutions are critical for handling business-critical applications and data:
- Dell EMC: Offers a range of servers, storage arrays, and hyper-converged infrastructure solutions.
- HP (Hewlett Packard Enterprise): Provides servers, storage systems, and networking equipment for various business needs.
These vendors offer scalable, high-performance solutions that can be tailored to specific organizational requirements.
Monitoring and Management Infrastructure
Effective network maintenance requires robust monitoring and management tools:
- Network monitoring software (e.g., SolarWinds, PRTG, Nagios) for real-time visibility into network performance.
- Configuration management tools for maintaining consistent settings across devices.
- Log management and analysis tools for troubleshooting and security monitoring.
- Automated alerting systems to notify IT staff of potential issues.
Implementing a comprehensive monitoring and management infrastructure enables proactive maintenance and rapid issue resolution.
,
Cloud Integration and Optimization
Integrating cloud services into existing infrastructure requires careful planning and optimization:
- Assessing which workloads are suitable for cloud migration.
- Implementing secure, high-performance connections between on-premises and cloud environments.
- Optimizing application performance in hybrid environments.
- Managing costs through effective resource allocation and monitoring.
- Ensuring data compliance and sovereignty requirements are met.
Proper cloud integration and optimization can lead to improved scalability, cost savings, and enhanced business agility.
Conclusion
Effective network planning and maintenance is crucial for modern businesses. By carefully considering physical infrastructure, leveraging cloud technologies, implementing robust security measures, and utilizing enterprise-grade equipment, organizations can build and maintain a network that supports their current needs and future growth. Regular monitoring, management, and optimization ensure that the network remains a valuable asset in driving business success.
Why SSP?
Partner Network
Modern Perspective
Understands the Bottom Line of Business

At SSP, we don't just fix IT issues; we architect digital ecosystems that propel your business forward.
By seamlessly aligning technology with your strategic goals, we create a synergy that transcends traditional IT support.
Our holistic approach doesn't just meet your current needs – it anticipates future challenges and opportunities.
With SSP, you're not just keeping pace; you're setting the rhythm of innovation. We don't simply support your vision; we expand its horizons, taking you beyond what you thought was possible.
Reimagine your IT landscape with SSP, where every solution is a stepping stone to your next breakthrough